Inbox
Move idea from "Submission and Collaboration" stage to:
Do you want to send this idea to AdaptiveWork?
Do you want to send this idea to Portfolios?
Which workspace template do you wish to use?
on
Executive Summary
Critical National Infrastructure are usually closed systems and humans are the most vulnerable and common attack vector. Employees and the general public are not trained in regards to defending against phishing attacks. Layer 8 is an open source phishing platform that helps to train and spread awareness about phishing and how to defend against it.
The problem
Critical national infrastructure providers and others are improving cyber security capabilities around industrial control systems. Operational technology typically does not have access to the rest of the world wide web, ensuring that they are in a mostly enclosed system. This however ignores the most important vulnerability of all, the human factor.OT(Operational technology) system operators are usually not cybersecurity trained and are not able to adequately appreciate the threats and risks. Cyber security professionals are usually more familiar with the IT environment and are not able to appreciate the different considerations and requirements of the OT environment.
Inspiration
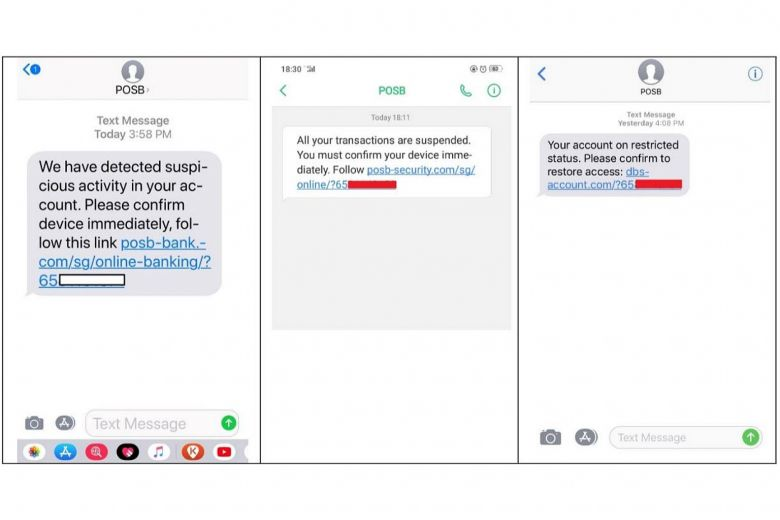
Our team consists of polytechnic students studying Information technology and cybersecurity in singapore, as such we have recently experienced a series of attacks on our health institutions which are a key part of singapore’s critical infrastructure. Some of us were personally affected by this attack and had our personal details stolen alongside millions of people including our prime minister. We found out that the infrastructure was segregated with no access to the rest of the Internet, however with the recent release of the public Report of the Committee of Inquiry, the initial breach vector was a phishing attack that gained access to front-end workstations from which they pivoted and managed to access the rest of the network with key resources such as the general public’s personal data. While performing volunteering and public outreach services, we realised that the general public were not aware of the dangers of cybersecurity and didn't realise they are the most vulnerable point of access and do not practice safe cybersecurity habits.
Statistics
Examples of recent operational technology system attacks include but are not limited to:
2019 - Singhealth (Singapore)
- Singhealth
2018 - Telecommunication System(Ukraine)
- According to the SBU(Ukraine security service), the attack had begun by sending emails with fake accounting documents attached to them designed to trigger stealthy information stealing malware when opened. This was alongside GreyEnergy, a malware that was targeting critical infrastructure in Ukraine via phishing
2017 - Petrochemical facilities (Middle East)
- Triton, a sophisticated malware, attacked safety instrumented systems, a critical component designed to protect human life. The initial vector of infection was likely a phishing attack. After gaining remote access, the attackers moved to disrupt, take down or destroy the industrial process.
2010 - Nuclear facilities (Iran)
- Stuxnet, a malicious computer worm, was believed to be responsible for causing substantial damage to Iran’s nuclear facilities. It specifically targeted Programmable Logic Controllers (PLCs) used to control centrifuges for separating nuclear material. The worm travelled via USB drives and reprogrammed PLCs to operate out of their controlled boundaries and sent false data to the operators to mask the activities.
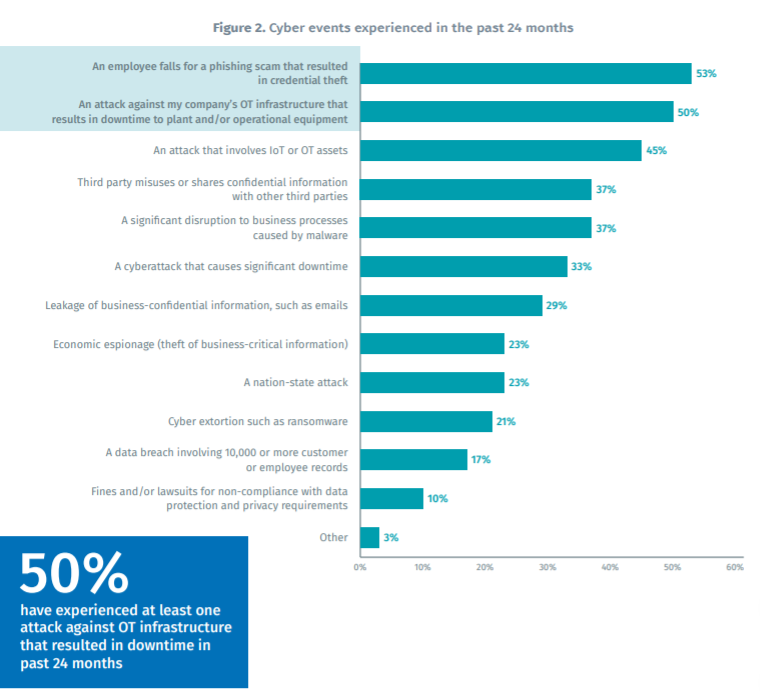
Phishing IT to access OT
Virtually all organizations in the OT(Operational Technology) sector rely on converged OT and IT(Information Technology) systems. Thus, the OT sector is concerned with weaknesses and attacks found in OT and IT systems, including phishing scams. 53% of OT sector organizations in a report (by Tenable 2019 March) state that in the past 24 months an employee fell for a phishing scam resulting in credential theft. OT attackers often use credentials gained in IT environments to pivot into and attack OT infrastructure.
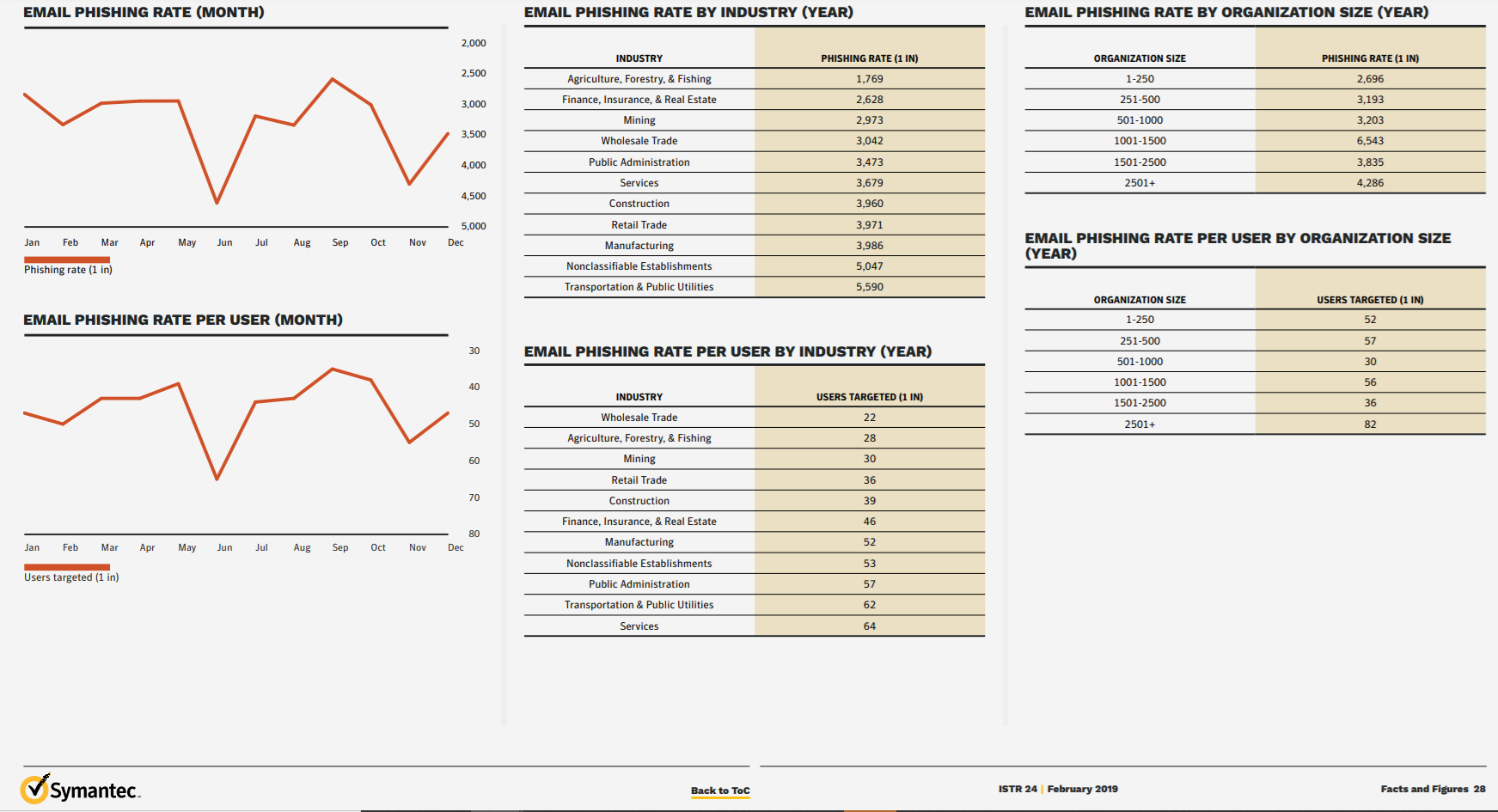
Odds of being Phished
Many people do not see the danger of being phished as they assume that the odds are tiny and negligible however in a report by Symantec 2019, 1 in every 3207 emails are a phishing email with key areas being targeted such as Public Administration with 1 in every 3473 and Transportation and Public Utilities with 1 in every 5590 emails being phishing emails.
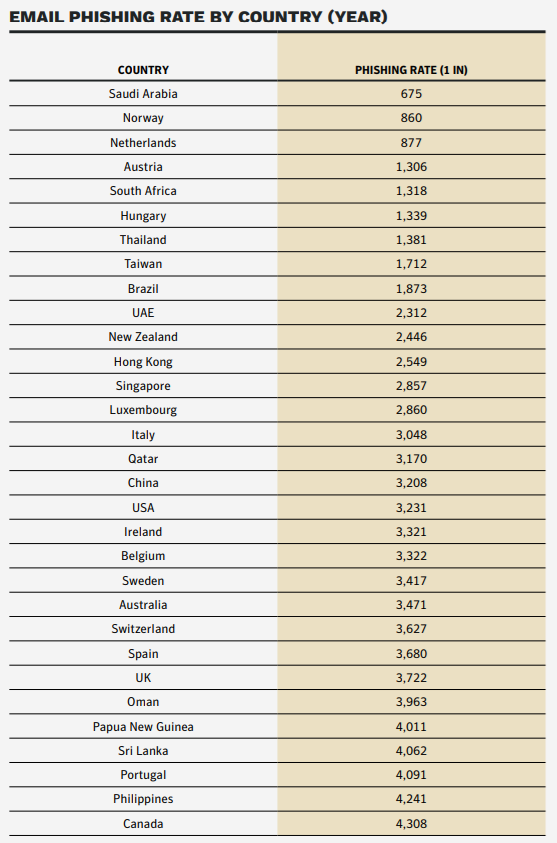
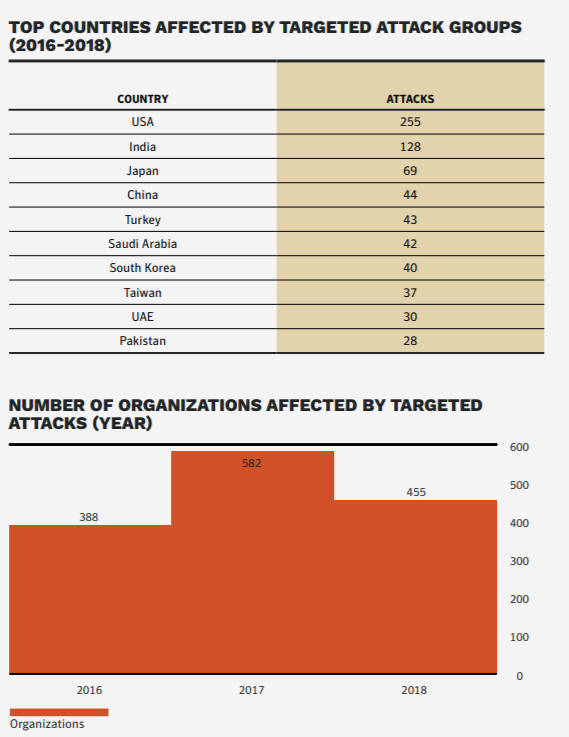
Countries in Asia, Middle East and Africa are particularly vulnerable to being phished due to the lack of cybersecurity standards and laws enforcing security and safe practices. Spear-phishing emails remained the most popular avenue for attack and were used by 65 percent of all known groups.
Impact of being Phished
84% of organizations said a spear-phishing attack successfully penetrated their organization
in 2015 and the average impact of a successful spear-phishing attack: $1.6 million. Victims saw their stock prices drop 15%.
APTs (Advanced Persistent Threats), attackers and terrorists use phishing as the return is much higher if criminals do their homework and target their victims with precision, expertly-crafted spear-phishing emails that can spoof senders and look completely legitimate.
Solution
Layer 8 is an open-source free phishing platform that can be used to perform phishing campaigns which will help to raise awareness for the general public and train the staff operating and working with critical infrastructure,ensuring that the employees are aware and trained against such attacks. Using VOIP(Voice over IP) technology and the insecure protocols that are used everyday such as emails, Layer 8 allows users to send fake smses, emails as well as fraudulent phone calls where the general public would not be able to tell the difference between a real and fake message. It allows for detailed customization so that the messages,emails and phone calls can be tuned to target a specific group of people such as employees of telecoms, power stations, hospitals or even nuclear power plants and military compounds or to the extent of targeting 1 specific individual.
Specifications
Frontend is built using Html5, CSS3 and bootstrap, Backend is made up of nodejs which handles the API calls, sending and receiving messages as well as hosting the web server. This ensures that the program is lightweight, easily deployable by anybody and easy to be built upon. The phishing is done using various libraries and VOIP APIs which are easy to set up and cheap. The program is cross platform and allows customization which enables it to have a large variety of use cases.
Additional details
Future Plans
We plan for Layer 8 to be integratable with external APIs and open source, allowing for the general public to use and build on this technology. Layer 8 should be able to be used by companies to train their staff and ensure that they won’t fall victim to phishing attacks as well as be used by government bodies to educate the general populace on the dangers of phishing.
Implementation
The program is meant to be easily set up and used purely from the frontend, ensuring good user experiences, however if the user wishes, they can delve into the code and add additional functionalities such as adapting it for their workplace if they have special system in place. Since it is built on Node.js, it is lightweight and can run on any device, whether from a low specification laptop or even a Raspberry Pi.
Viability
We came up with this idea as even though there are companies that provide phishing campaigns for companies, usually they are very costly and rarely customisable, this enables activists and communities to perform the phishing awareness raising by themselves without much cost and encourages companies to train their staff as well and allows for better training than any company provided phishing campaign as it is customizable.
Sources
Raf.mod.uk. (2019). [online] Available at: https://www.raf.mod.uk/what-we-do/centre-for-air-and-space-power-studies/documents1/dissertation-lydiate-dan-mstrat-dissertational1/ [Accessed 15 Nov. 2019].
Parameswaran, P. (2019). ASEAN Cybersecurity in the Spotlight Under Singapore’s Chairmanship. [online] Thediplomat.com. Available at: https://thediplomat.com/2018/05/asean-cybersecurity-in-the-spotlight-under-singapores-chairmanship/ [Accessed 15 Nov. 2019].
Compendium(2018) [online] Available at:
https://www.un.org/sc/ctc/wp-content/uploads/2018/06/Compendium-CIP-final-version-120618_new_fonts_18_june_2018_optimized.pdf [Accessed 15 Nov. 2019]
Resolution 284(2018)[online] Available at:
https://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/72/284 [Accessed 15 Nov. 2019]
Resolution 288(2018) [online] Available at:
https://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/60/288 [Accessed 15 Nov. 2019]
Icitech(2019)[online] Available at:
https://icitech.org/wp-content/uploads/2019/05/ICIT-Cyber-Legislation-Report-Sample.pdf
IBM OT(2019)[online] Available at:
https://www.ibm.com/security/operational-technology [Accessed 15 Nov. 2019]
Ministerial Statement(2019)[online] Available at:
https://www.channelnewsasia.com/news/singapore/singhealth-cyberattack-ministerial-statement-coi-recommendations-11125014 [Accessed 15 Nov. 2019]
PWC OT(2019)[online] Available at:
https://www.pwc.com/sg/en/risk-assurance/operational-technology.html [Accessed 15 Nov. 2019]
CSA (2019)[online] Available at:
https://www.csa.gov.sg/gosafeonline/go-safe-for-me/homeinternetusers/top-10-ways-to-defend-against-phishing [Accessed 15 Nov. 2019]
MCI Report(2019)[online] Available at:
https://www.mci.gov.sg/~/media/mcicorp/doc/report%20of%20the%20coi%20into%20the%20cyber%20attack%20on%20singhealth%2010%20jan%202019.pdf?la=e [Accessed 15 Nov. 2019]
Report(2019)[online] Available at:
https://www.symantec.com/content/dam/symantec/docs/reports/istr-24-2019-en.pdf [Accessed 15 Nov. 2019]
Fireeye (2019)[online] Available at:
https://www.fireeye.com/content/dam/fireeye-www/global/en/products/pdfs/wp-fireeye-how-stop-spearphishing.pdf[Accessed 15 Nov. 2019]
Gartner Mimecast(2019)[online] Available at:
https://www.gartner.com/imagesrv/media-products/pdf/mimecast/Mimecast-1-4QT9Y3H.pdf[Accessed 15 Nov. 2019]
UN Press(2019)[online] Available at:
https://www.un.org/press/en/2017/sc12714.doc.htm[Accessed 15 Nov. 2019]
Chye Mun Kiat,Sean;Clarabel Teo JingHui
https://github.com/Nonsouris/Layer-8
Raf.mod.uk. (2019). [online] Available at: https://www.raf.mod.uk/what-we-do/centre-for-air-and-space-power-studies/documents1/dissertation-lydiate-dan-mstrat-dissertational1/ [Accessed 15 Nov. 2019]. Parameswaran, P. (2019). ASEAN Cybersecurity in the Spotlight Under Singapore’s Chairmanship. [online] Thediplomat.com. Available at: https://thediplomat.com/2018/05/asean-cybersecurity-in-the-spotlight-under-singapores-chairmanship/ [Accessed 15 Nov. 2019]. Compendium(2018) [online] Available at: https://www.un.org/sc/ctc/wp-content/uploads/2018/06/Compendium-CIP-final-version-120618_new_fonts_18_june_2018_optimized.pdf [Accessed 15 Nov. 2019] Resolution 284(2018)[online] Available at: https://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/72/284 [Accessed 15 Nov. 2019] Resolution 288(2018) [online] Available at: https://www.un.org/en/ga/search/view_doc.asp?symbol=A/RES/60/288 [Accessed 15 Nov. 2019] Icitech(2019)[online] Available at: https://icitech.org/wp-content/uploads/2019/05/ICIT-Cyber-Legislation-Report-Sample.pdf IBM OT(2019)[online] Available at: https://www.ibm.com/security/operational-technology [Accessed 15 Nov. 2019] Ministerial Statement(2019)[online] Available at: https://www.channelnewsasia.com/news/singapore/singhealth-cyberattack-ministerial-statement-coi-recommendations-11125014 [Accessed 15 Nov. 2019] PWC OT(2019)[online] Available at: https://www.pwc.com/sg/en/risk-assurance/operational-technology.html [Accessed 15 Nov. 2019] CSA (2019)[online] Available at: https://www.csa.gov.sg/gosafeonline/go-safe-for-me/homeinternetusers/top-10-ways-to-defend-against-phishing [Accessed 15 Nov. 2019] MCI Report(2019)[online] Available at: https://www.mci.gov.sg/~/media/mcicorp/doc/report of the coi into the cyber attack on singhealth 10 jan 2019.pdf?la=e [Accessed 15 Nov. 2019] Report(2019)[online] Available at: https://www.symantec.com/content/dam/symantec/docs/reports/istr-24-2019-en.pdf [Accessed 15 Nov. 2019] Fireeye (2019)[online] Available at: https://www.fireeye.com/content/dam/fireeye-www/global/en/products/pdfs/wp-fireeye-how-stop-spearphishing.pdf[Accessed 15 Nov. 2019] Gartner Mimecast(2019)[online] Available at: https://www.gartner.com/imagesrv/media-products/pdf/mimecast/Mimecast-1-4QT9Y3H.pdf[Accessed 15 Nov. 2019] UN Press(2019)[online] Available at: https://www.un.org/press/en/2017/sc12714.doc.htm[Accessed 15 Nov. 2019] https://github.com/Nonsouris/Layer-8

Help to Improve This Idea.