Inbox
Move idea from "Submission and Collaboration" stage to:
Do you want to send this idea to AdaptiveWork?
Do you want to send this idea to Portfolios?
Which workspace template do you wish to use?
on
With advancing age, social media has become the ultimate “constructive” novelty. However, calling it constructive, in most cases, is nothing but a euphemistic term for extremist groups (terrorist).
Communication is the key element in executing a plan. To achieve its goal, a terrorist group must be clear in its communications. Social media is the main tool assisting in all kinds of communication. Ceasing all contact can greatly affect their plans.
Therefore, our system is specially designed to analyze text written in any messages across several messenger services and decide whether it is categorized as hateful or not. This analysis is conducted using a database consisting of potential hateful words or phrases – a specialized dictionary aided with machine learning for the constant updates in the dictionary this will further allow to add in code-language. Built on decentralized blockchain technology that ensures data is tamper proof.
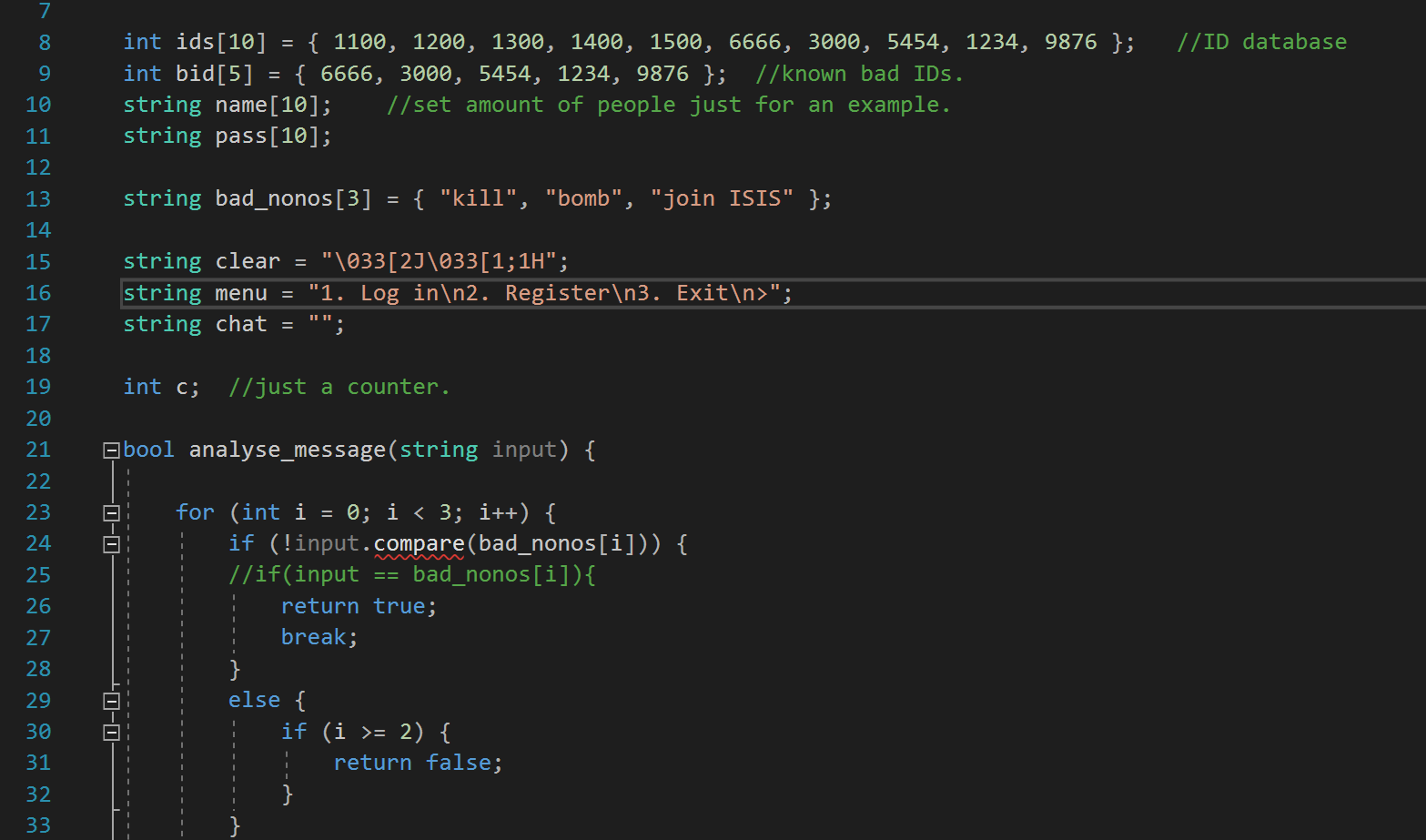
Line 13 is a part of our program code that shows the dictionary of offensive words.
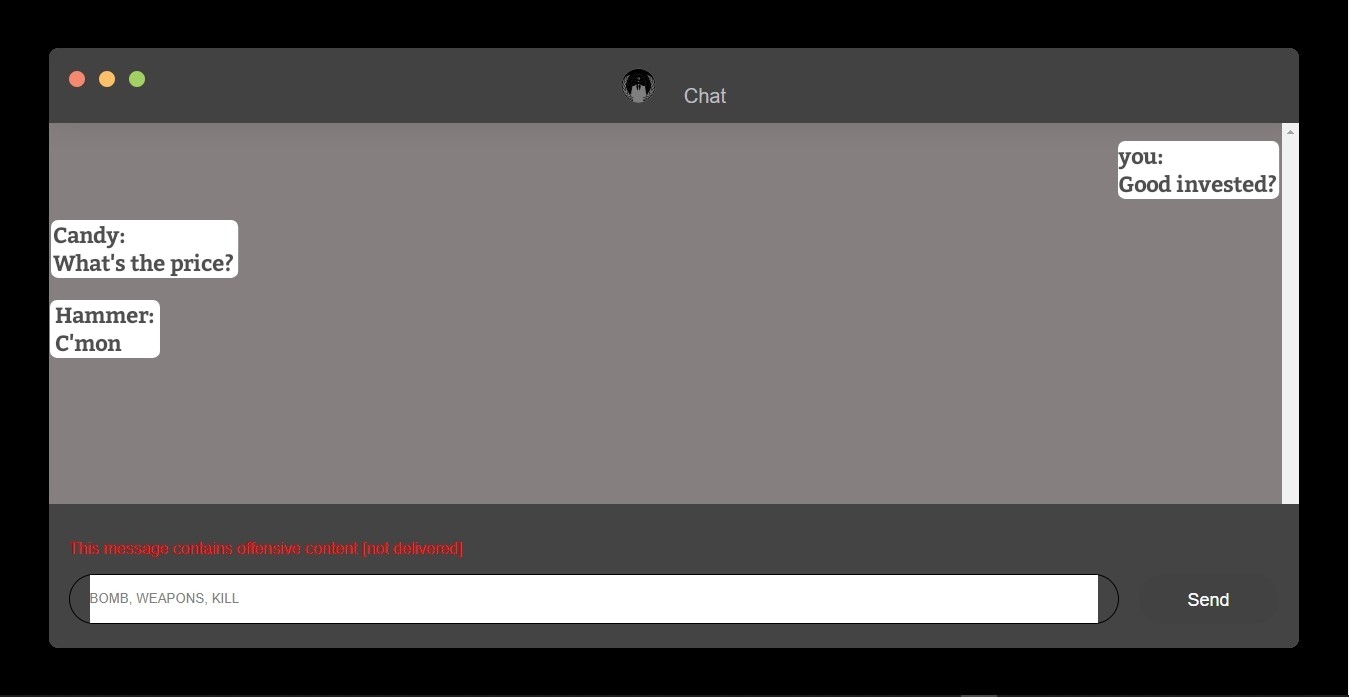
This is an example of a chat in any messenger service. It showcases how our program will disable any sharing of hateful content.
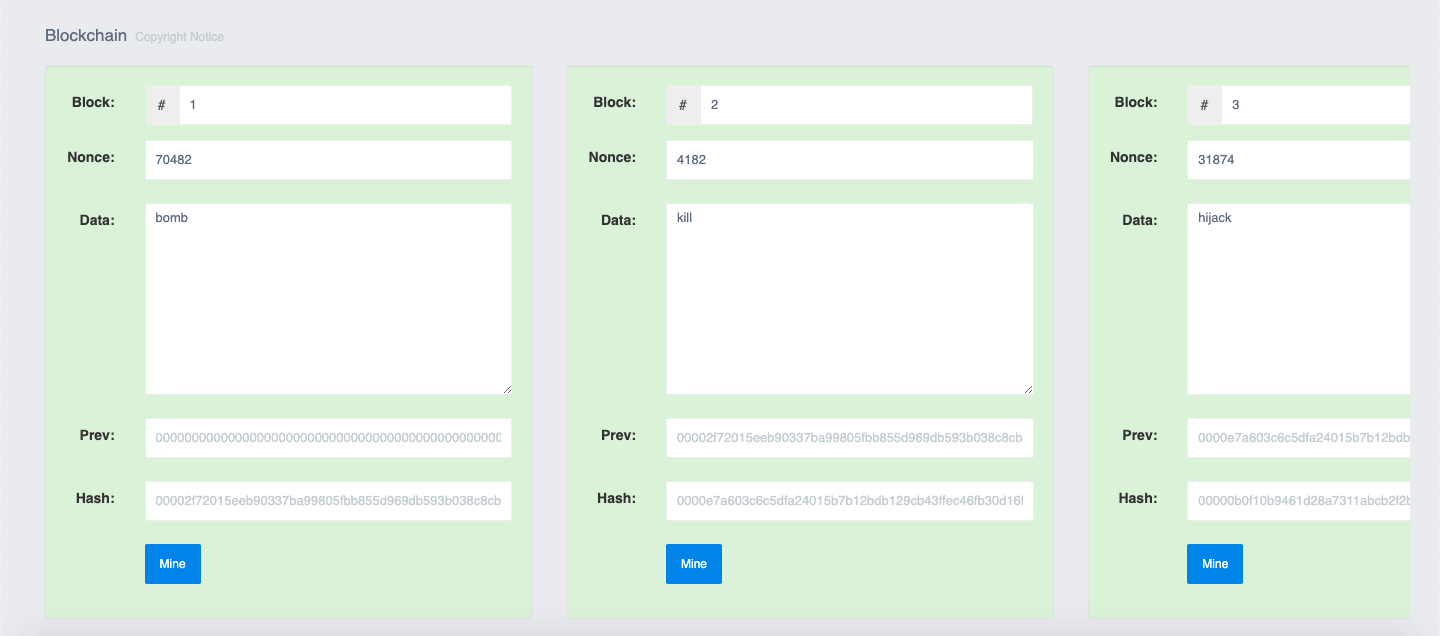
The above snapshot is of the Blockchain technology being utilized to store the offensive words in each block, providing a highly secure platform for decentralized data storage.
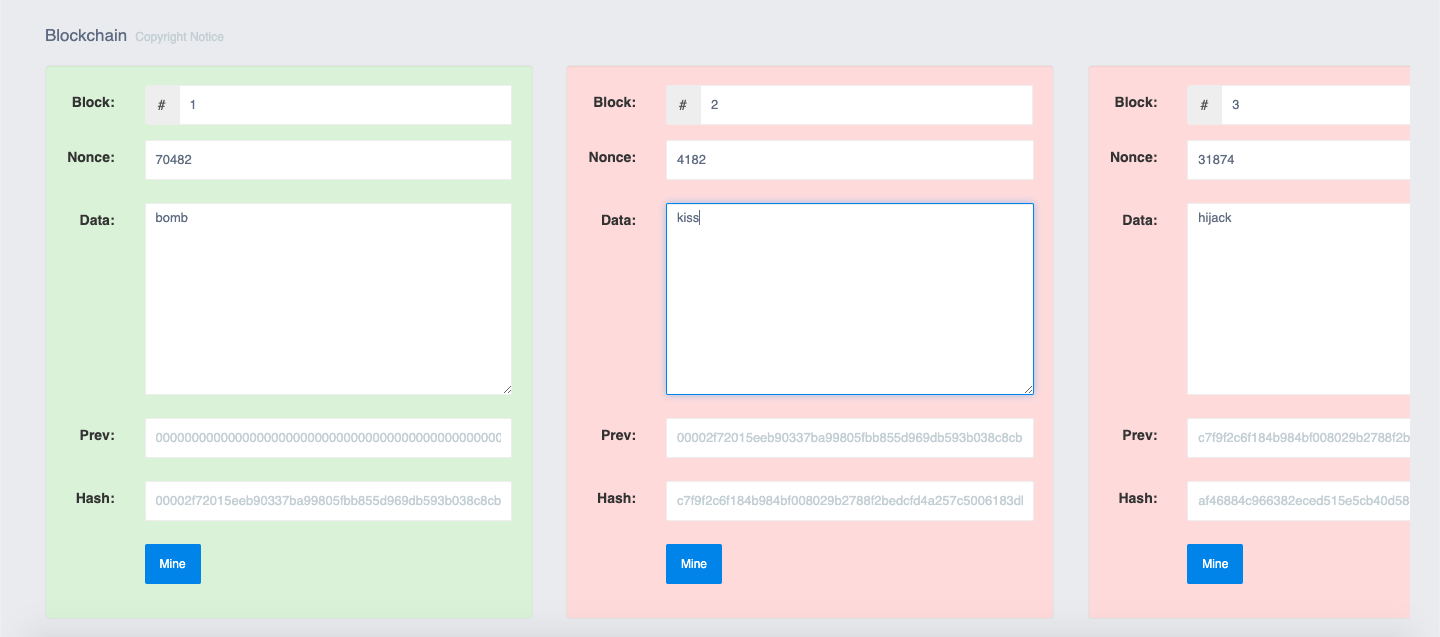
Further, the above snapshot proves the security of blockchain by alarming the tampering of changes in data of the block. For instance a terrorist hacks into the blockchain network and replaces the word 'kill' with 'kiss' this will be immediately detected.
Another factor promoting sharing of hateful and offensive content is through fake identities. Our system eliminates creation of these profiles to not only keep online platforms secure but also to enforce abortion of any harmful plans. Blockchain will be utilized to store the credentials.
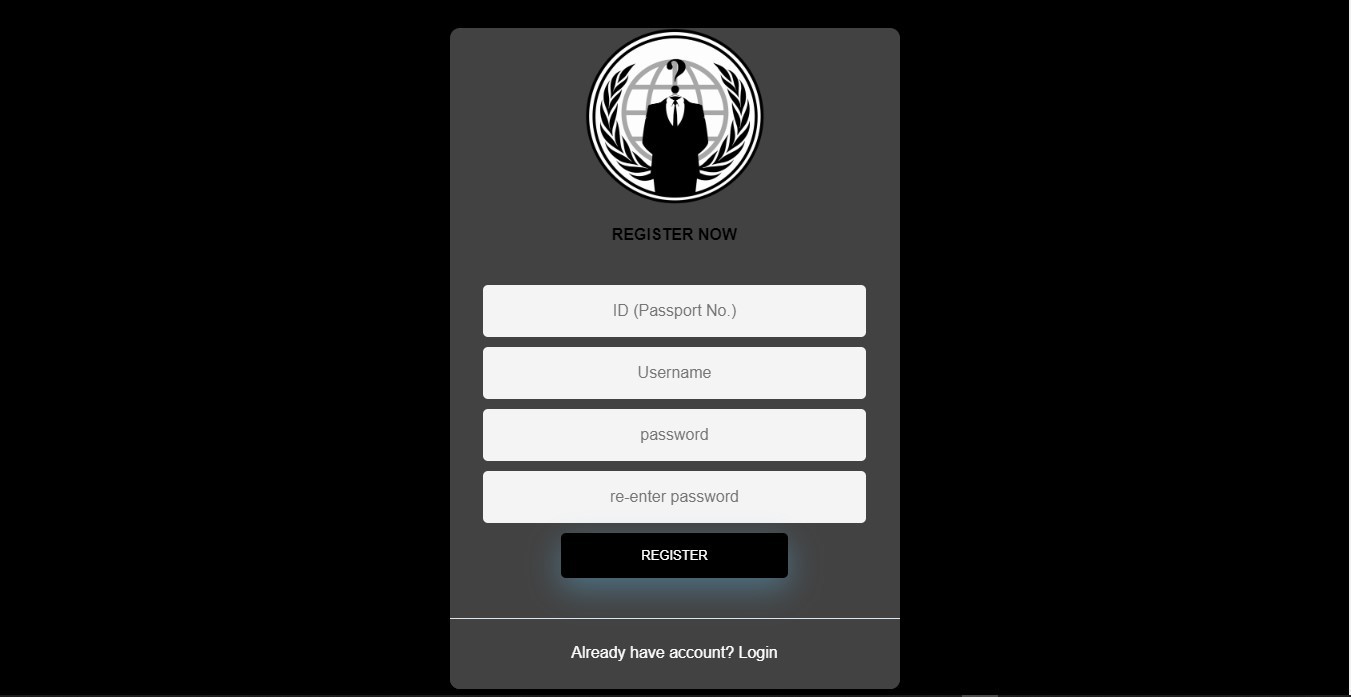
This image shows the registration page. Note that it is a compulsion to add the passport number. This is to ensure the relevance of identity.
Through this platform, we aim to prevent terrorist activities by cutting off their transmission and enforcing a barrier. Eliminating terrorists content and communication from online sites has become a necessity. Our program enables youth to a more secure network to connect with each other. The system promotes safe space for communication among youth and blocks any terrorist organisation get in touch with young people to harm their vision in any way. This communication barrier will lead to promotion of world peace.
Sara Shafique, Abdullah Ansari, Azhar Jeetun, Muhammad Qasim
https://docs.google.com/document/d/1WN1tER2DIcL8YlCp2rJO7YpFmjKh-ZGAT-3MVfRBFw8/edit
https://cloudmails-my.sharepoint.com/personal/tp050507_mail_apu_edu_my/_layouts/15/onedrive.aspx?id=/personal/tp050507_mail_apu_edu_my/Documents/files.zip&parent=/personal/tp050507_mail_apu_edu_my/Documents&originalPath=aHR0cHM6Ly9jbG91ZG1haWxzLW15LnNoYXJlcG9pbnQuY29tLzp1Oi9nL3BlcnNvbmFsL3RwMDUwNTA3X21haWxfYXB1X2VkdV9teS9FUnhmaDdGdC1iQk9uR1k5M2E3S1BVb0JVVFR0ZWRPUzMyYlNjM2ZMS0lxTVNRP3J0aW1lPVRsbHBrd3hxMTBn
The reference link have been provided in the documentation. Please access through the link provided.

Help to Improve This Idea.