Inbox
Move idea from "Submission and Collaboration" stage to:
Do you want to send this idea to AdaptiveWork?
Do you want to send this idea to Portfolios?
Which workspace template do you wish to use?
on
Problem Statement
The terrorist organizations such as ISIS, Al-Qaeda are using internet especially social media to find out people who are angry/dissatisfied with any government or particular community or the people who can be easily brainwashed to join their causes in a variety of ways. These organizations release contents(doctored videos, posts, blogs etc.) that are influencing people especially innocent youth. Statistics shows the tremendous increase in the presence of these terror groups on internet in past few years. They use websites and social media platforms to share propaganda (information that is shared and spread in order to influence public opinion and to manipulate other people's beliefs, often to promote or publicize a particular political cause or point of view) and to foster a sense of community for supporters, especially when trying to entice young people to their cause. Many terrorist groups have their own websites and their supporters have profiles on different social media handles. They use internet to share propaganda and to become friends with people who seem to display some interest in what they are saying. The very first conversation between these organization and the brain washed people/youth mainly takes place using social media handles, specially Facebook. This newly brainwashed youth/person is continuously spied and their online behavior is analyzed to confirm whether they are ready for the next step i.e. complete brainwash and training by terrorist organizations. After confirmation, the brainwashed youth is provided with the local support to reach the training location or the visual training.
Media plays a very big role in influencing these youths to get converted into a terrorist, televisions and online platforms are flooded with hate and violent contents which ultimately lessen the work of these organizations.
Objectives
- To defend the expansion of terrorist organizations.
- To defend the brainwashing of innocent people through hateful and violent doctored contents on the internet.
- To develop a system that will detect and alarm the defense/secret agencies about internet users who can be easily influenced by violent, hate or terrorist content to join extremist groups .
- To halt brainwashing of internet user by showing emotional and factual based content.
- To stop online recruitment of terrorist.
Solution
As a matter of fact, social media is considered as essential today. According to Global Digital 2019 report, almost 4.388 billion users are present on internet whereby 3.484 billion people uses social media actively.
According to the problem statement, the presence of the terrorist organizations such as Al-Qaeda, ISIS, etc. has increased tremendously on internet. The solution to this problem requires forming a team of data analysts and Machine Learning experts which will work closely with defense/secret agencies of the government. This team of data analysts will keep an eye on internet especially on social media handles such as Facebook, Instagram, Twitter, etc.
The proposed solution will use Machine Learning algorithms to categories the contents on internet such as violent content, hateful content, terror content, etc. Whenever the machine learning algorithm finds a content related to violence, hate or terrorism then it automatically put those content into their respective category. A limit will be established on frequency of actions (views, likes, etc.) taken on such contents. Advanced data analytics is used to record the type and the frequency of content a user views, shares, likes, etc. The system automatically detects and alarms the agencies once a user views, likes or shares a hateful, violent, terror-related content more than the specified frequency. If the user enters in the risk zone, the team starts profiling him/her according to his/her internet behavior using data analytics. The solution does not only focus on detecting people getting influenced by terrorist organizations but also defending it. Once the team confirms a user that is prone to brainwashing, the team starts sending targeted positive contents to the users in the form of advertisement and recommendations. These contents would be comprised of factual motivational videos, news, images, blogs, etc. Human being is a social animal and they can be easily manipulated by emotions therefore, many emotional contents will be shown to the user to stop his/her brainwashing.
Given below are two examples of such emotional content that can heavily impact a human mind:
Faqr Hai (YouTube Link): https://youtu.be/CwAi19Ev2bg
Jihad Hai (YouTube Link): https://youtu.be/jhCo2VNH_5w
The above YouTube videos are produced in Hindi language by Indian production houses, it is related to terrorism and it has very deep psychological ending with a positive message. Contents like these can be produced in different languages based on various emotions to be used in various cultural region.
This system will only access user’s data that will be identified by the Machine learning algorithm and that falls in such categories (Hateful content, Terror-content, etc.) while respecting the data privacy of internet users.
Working of the solution
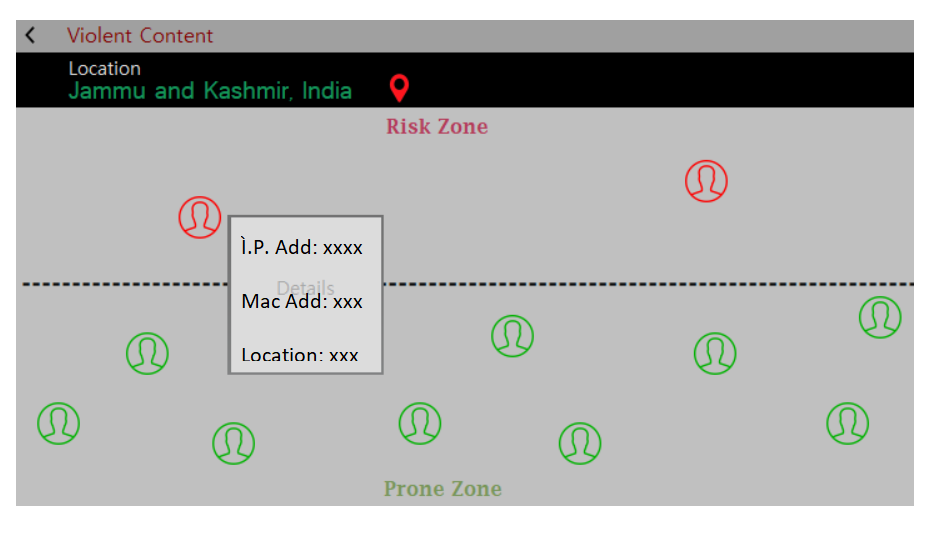
The above picture is a prototype of the real system. The system will have multiple windows such as “Violent Content, Hate Content and Terror Content” window.
Each window has two sections (Risk Zone & Prone Zone), the profiles in the Prone Zone are considered as safe while profiles in the Risk Zone are at high risk of getting manipulated or influenced. The dotted line is frequency limit for that particular content.
Data analysis will be used to count the number of times a particular user views, likes, access, etc. contents from the above categories. Once a user access, views, shares, likes, etc. such kind of contents more than the specified frequency, the system will alarm and the user is displayed in the risk zone.
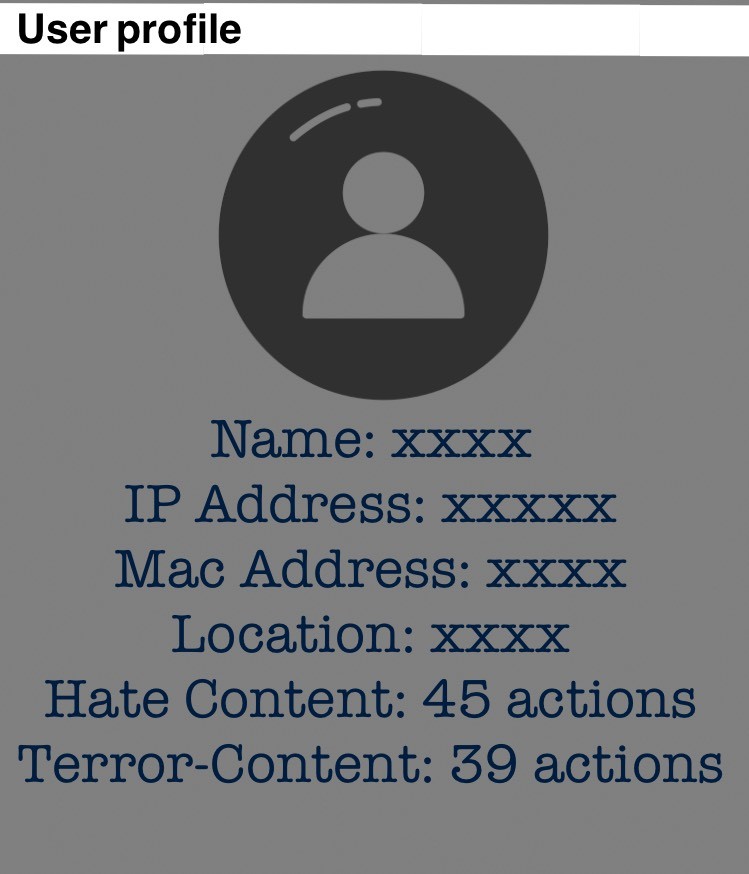
The team starts profiling the user based on his/her internet behavior and starts sending targeted positive contents to the user in the form of advertisement and recommendation.
Another window using map will show users in the Risk Zone and their location on the map.
References
- https://arxiv.org/ftp/arxiv/papers/1702/1702.02263.pdf
- http://mmm2019.iti.gr/large-scale-big-data-analytics-for-online-counter-terrorism-applications-ss4cta/
- https://firstmonday.org/ojs/index.php/fm/article/view/7126/6522
- https://www.adl.org/education/resources/tools-and-strategies/table-talk/propaganda-extremism-online-recruitment
Parvez Alam, Vaibhav Arora, Abhishek Yadav
https://drive.google.com/open?id=15ECtOhnjTXClPqAPtYpulKxRkNDP54tG

Help to Improve This Idea.